The Future of Data: LinkDaddy Universal Cloud Storage Press Release Explained
The Future of Data: LinkDaddy Universal Cloud Storage Press Release Explained
Blog Article
Browsing the Information Privacy Landscape: Just How Universal Cloud Storage Space Solutions Can Aid
In today's electronic age, protecting delicate data has actually become an extremely important problem for companies and individuals alike. As the data privacy landscape proceeds to develop, the requirement for robust solutions to safeguard secret information has never ever been a lot more important. Universal cloud storage space services supply an engaging opportunity for browsing this complex terrain, providing a secure and functional platform for data monitoring. By discovering the crossway of data personal privacy and cloud storage space, a deeper understanding arises of exactly how these services can not just improve safety but additionally enhance operations in an increasingly interconnected globe.
Relevance of Information Personal Privacy Defense
Ensuring durable information privacy protection is extremely important in securing delicate info in today's interconnected digital landscape. With the exponential development of information collection and sharing, the danger of unauthorized accessibility and abuse of private and personal data has become a common issue. Data privacy violations not only jeopardize people' privacy yet also have serious implications for organizations, including economic losses, reputational damages, and legal consequences.
Effective information personal privacy protection entails executing strict safety measures to stop unauthorized access, making certain compliance with information defense guidelines, and fostering a culture of personal privacy recognition among customers - universal cloud storage Service. By prioritizing information privacy, companies can build trust fund with their stakeholders and clients, showing their dedication to protecting delicate info
In addition, in an era where data is thought about the brand-new money, maintaining information personal privacy is essential for protecting individuals' autonomy and stopping prospective misuse of personal info for targeted advertising and marketing, identity burglary, or various other malicious purposes. Investing in durable data personal privacy security mechanisms is not only a lawful demand but also a tactical imperative for businesses running in today's data-driven environment.
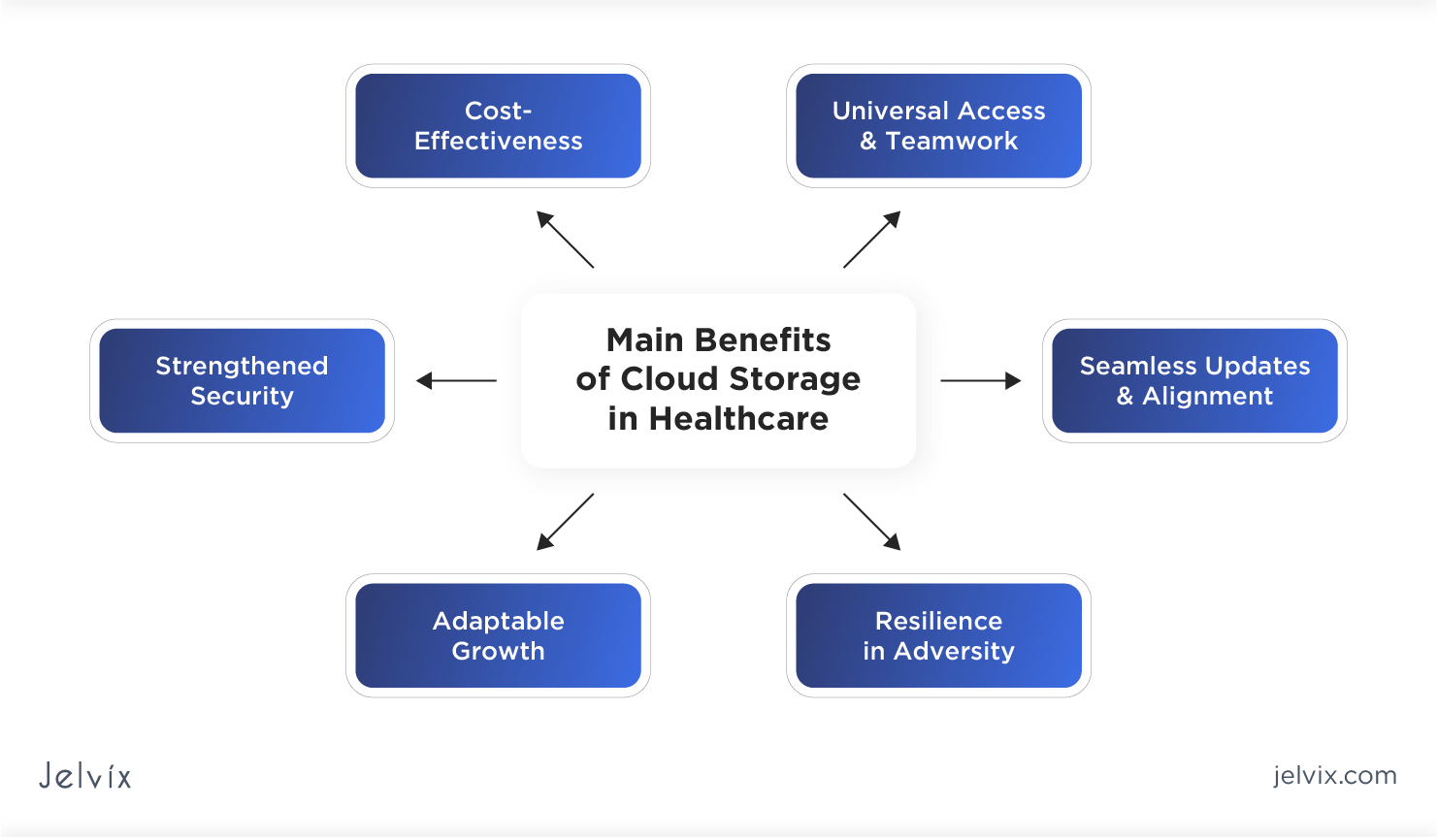
Advantages of Universal Cloud Storage Space
Universal Cloud Storage offers unrivaled scalability and flexibility for keeping and accessing data safely across different devices and areas. One of the vital benefits of global cloud storage is the capacity to scale storage space capacity based on demands without the headache of physical upgrades or constraints. This indicates that businesses can conveniently adjust their storage needs as data quantity grows, making sure cost-effectiveness and efficiency.
One more benefit is the flexibility it gives in accessing data from anywhere, at any moment, and from any tool with an internet link. This accessibility promotes cooperation among group participants situated in different geographical places and enables remote job capacities. Furthermore, universal cloud storage space services commonly come with sophisticated protection features such as file encryption, accessibility controls, and routine back-ups, guaranteeing data defense and compliance with personal privacy regulations.
Moreover, universal cloud storage space eliminates the requirement for physical storage space devices, minimizing hardware costs and upkeep initiatives. By leveraging the cloud for storage demands, organizations can enhance data monitoring processes and concentrate on core service activities.
Improved Information Safety Measures
Carrying out durable data file encryption protocols is vital in guarding sensitive information stored on global cloud storage systems. In addition to security, multi-factor verification adds an additional layer of safety and security by needing individuals to offer several kinds of confirmation before accessing data.

Access and Convenience Functions
In the world of cloud storage space services, beyond the fundamental layer of boosted data safety and security gauges lies a vital emphasis on including functions that prioritize accessibility and benefit for individuals. Comfort attributes streamline individual experience by allowing smooth documents syncing throughout tools, intuitive folder organization, and quick access of stored information via durable search capabilities. These features not only help with reliable information monitoring yet additionally add to an user-friendly experience that promotes performance and partnership in both specialist and individual setups.
Compliance and Regulative Factors To Consider
Additionally, industry-specific criteria like the Repayment Card Industry Information Security Requirement (PCI DSS) for financial deals and the ISO/IEC 27001 for details safety and security monitoring better emphasize the demand for durable conformity actions. Failing to meet these needs can lead to serious consequences, including substantial fines, legal repercussions, and reputational damage. For that reason, cloud storage companies should apply strict policies, security methods, gain access to universal cloud storage press release controls, and regular audits to ensure recurring conformity and reduce potential threats linked with data breaches and non-compliance.
Verdict
To conclude, universal cloud storage space services supply a useful solution for browsing the complex information privacy landscape. With boosted safety measures, hassle-free ease of access attributes, and considerations for conformity and guidelines, these services supply a secure and reliable way to shop and safeguard delicate information - universal cloud storage Service. By using global cloud storage, services and individuals can secure their information while also making sure compliance with data security regulations and policies
With the exponential development of data collection and sharing, the threat of unauthorized accessibility and abuse of personal and personal information has come to be a common concern. In addition, universal cloud storage space services often come with advanced protection features such as security, access controls, and normal backups, making certain information protection and conformity with privacy guidelines.
Implementing rigorous access manages based on the concept of least privilege makes certain that individuals just have access to the information required for their duties, decreasing the danger of deliberate or unintended data breaches.

Report this page